Cryptography & its Uses
Relevance: Prelims/Mains: G.S paper III: Science and technology: Science and Technology- developments and their applications and effects in everyday life • Achievements of Indians in science & technology; indigenization of technology and developing new technology. • Awareness in the fields of IT, Space, Computers, robotics, nano-technology, bio-technology.
Introduction:
- Secured concern for diplomats, military, and other officials over the ages. Even if it’s exact origin cannot be traced back communication has always been an area of precisely, its importance can surely be understood from the fact that even the greatest rulers like Julius Ceasar had such a method for information exchange popularly named after him as Caesar Cipher.
About:
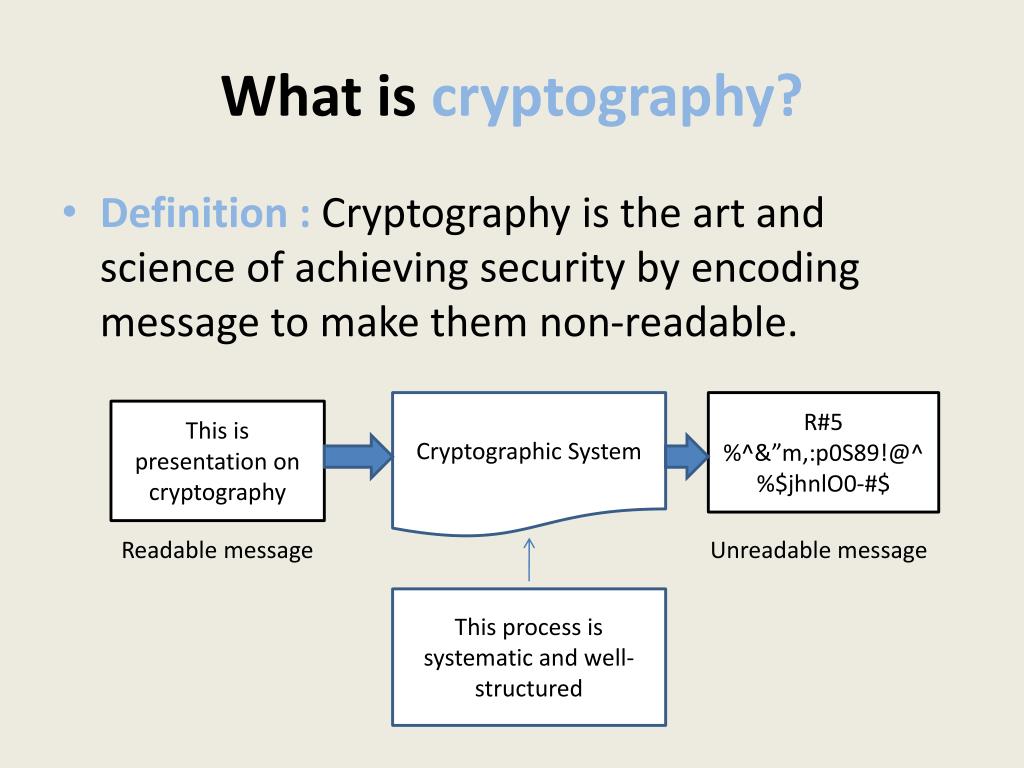
- The process of securing information by manipulating it in such a way that makes it incomprehensible for people unaware of the secret is called cryptography. Cryptography is a combination of two Greek words, cryptos meaning secret, and graphein meaning writing. So, in other words, cryptography can also be called secret writing.
• The technique is mainly based on a set of steps to be followed sequentially to achieve the incomprehensibility. These steps together constitute an algorithm. The algorithm takes meaningful information known as plaintext and converts it into a gibberish data called ciphertext.
• Mostly this conversion might require an additional piece of secret information known as a key whose knowledge is essential for securing and revealing the information. This process is known as encryption and decryption respectively.
• Depending upon the period, cryptography can be broadly categorized as Classical cryptography and Modern Cryptography. 
Classical Cryptography:
- Classical cryptography refers to the early form of the methodology which was mostly dependent on the rearrangement and the substitution of the letters in a way that the output could not be understood without the prior knowledge of the process.
• These forms of cryptography were very popular in ancient Egypt and Greece. The popular Caesar cipher is one of the oldest examples of the substitution cipher in which the letters of the plaintext were replaced by the letters in the alphabets starting from any specific place in the sequence.
Example: Let us assume that we replace each letter in a given plaintext with a new letter obtained by moving three places from the current letter in the English alphabet to obtain the ciphertext.
Plaintext: we are safe.
Ciphertext: zh duh vdih.
Modern Cryptography:
- Modern cryptography is primarily based on mathematical calculations that are easy enough to be carried out by a computer using a key but hard enough to be guessed in the absence of the same key. Claude E. Shannon is considered to be the father of this mathematical form of cryptography that led to the origin of the modern ciphers.
• Current cryptosystems work on the Kerckhoff’s principle which emphasizes on exposing everything related to the cipher in the public domain (including the algorithm) except for the
key. This means that the actual security of the data relies on the strength of the key used for encryption. Hence, for a modern cipher that is free from any design flaws, the length of the key used (in bits) will give an idea about the number of possible keys to be tried to break the security.
For example, if the key length used by an algorithm is 8 bits then there would be 28 i.e. 256 possible key combinations that need to be tried to reveal the information using brute-force.
Symmetric Key algorithms:
- These are algorithms that use the same key for the encryption and the decryption process and hence require the key being shared among all the individuals who need to have access to the data. Since the secrecy completely depends on the key being used, any accidental disclosure of the same to non-authorized individuals might lead to compromise of the entire system.
• This problem of safe key exchange is the greatest challenge associated with this method making it suitable only for securing data for an individual or a small group of people when this approach is not associated with any other special protocol for information exchange.
• Example: DES, AES-128, AES-256, Blowfish, IDEA, Twofish, etc. 
Asymmetric Key algorithms:
- These are algorithms that use a pair of keys for the encryption and decryption of the data – the keys are known as the public key and private key, respectively. The private key is kept a secret with the owner and is used to decrypt the data encrypted with the public key made available to everyone in the public domain. Another use of this type of algorithm is for user authentication where the data encrypted with the private key can be decrypted with the public key to verify the fact that only the owner of the private key can encrypt the data.
• Since this type of algorithm doesn’t rely on a single key for security, it overcomes the limitation of the symmetric key algorithms and is used for information exchange on the internet as a part of various information exchange protocols. One of the major limitations of these algorithms as compared to symmetric algorithms is that they are computationally expensive hence using them frequently within a process is not easy. 
Cryptographic Research in India:
- Cryptography along with information security being one of the hottest topics in the current times has made a huge impact within the Indian research fraternity as well. India with the motive of gaining excellence and promoting knowledge in this domain has set up some of the world’s best institutes like RC Bose Centre for Cryptology and Security at Kolkata.
• Organisations like Cryptology Research Society of India (CRSI) and Scientific Analysis Group (SAG) of the Defence Research & Development Organisation (DRDO) also do a lot of research in this field. The popular international cryptography conference called Indocrypt has been organized by CRSI every year since 2000 for the promotion of cryptography in India and abroad.
• Specialisation courses in cryptography and its associated fields are also offered at various IITs like IIT Kharagpur and IIT Madras for youngsters seeking a career in this domain.
• There is a need for official guidelines from the government on the standardization of the algorithms and cipher suites to be used to safeguard the personal data collected by the government and private entities from individuals to ensure a minimum level of standardized data security within the country. And of course, spreading awareness of the subject among the people is very essential to remain happy, healthy, and safe in cyberspace.
For more such notes, Articles, News & Views Join our Telegram Channel.
Click the link below to see the details about the UPSC –Civils courses offered by Triumph IAS. https://triumphias.com/pages-all-courses.php

